SpyderTracks
We love you Ukraine
This needs some attention, would highly recommend everyone install the latest Windows patches, and if you can, find the dedicated Microcode updates from Intel.
 techcrunch.com
techcrunch.com

 gizmodo.com
gizmodo.com
 www.zdnet.com
www.zdnet.com
Yet another serious flaw in Intel chips, and the patches will again have a negative impact on performance, currently estimated around 3% for normal windows users, up to 9% for datacenters and virtualised instances.
In itself, it doesn't seem that bad, but factor in Spectre and Meltdown patches, and we're looking at performance loss over 20%.
This is totally unacceptable.
I won't be buying Intel again until they address these flaws at the hardware level. Remember, even 9th Gen still doesn't patch the Spectre/Meltdown vulnerabilities, they've not done any redesign to mitigate those flaws.
Totally unacceptable imho.

New secret-spilling flaw affects almost every Intel chip since 2011 | TechCrunch
Security researchers have found a new class of vulnerabilities in Intel chips which, if exploited, can be used to steal sensitive information directly

What To Do About the Nasty New Intel Chip Flaw
An entire class of vulnerabilities in Intel chips allows attackers to steal data directly from the processor, according to new reports from a group of cybersecurity researchers from around the world. Intel, Apple, Google and Microsoft among other tech giants have released patches to address the...
 gizmodo.com
gizmodo.com

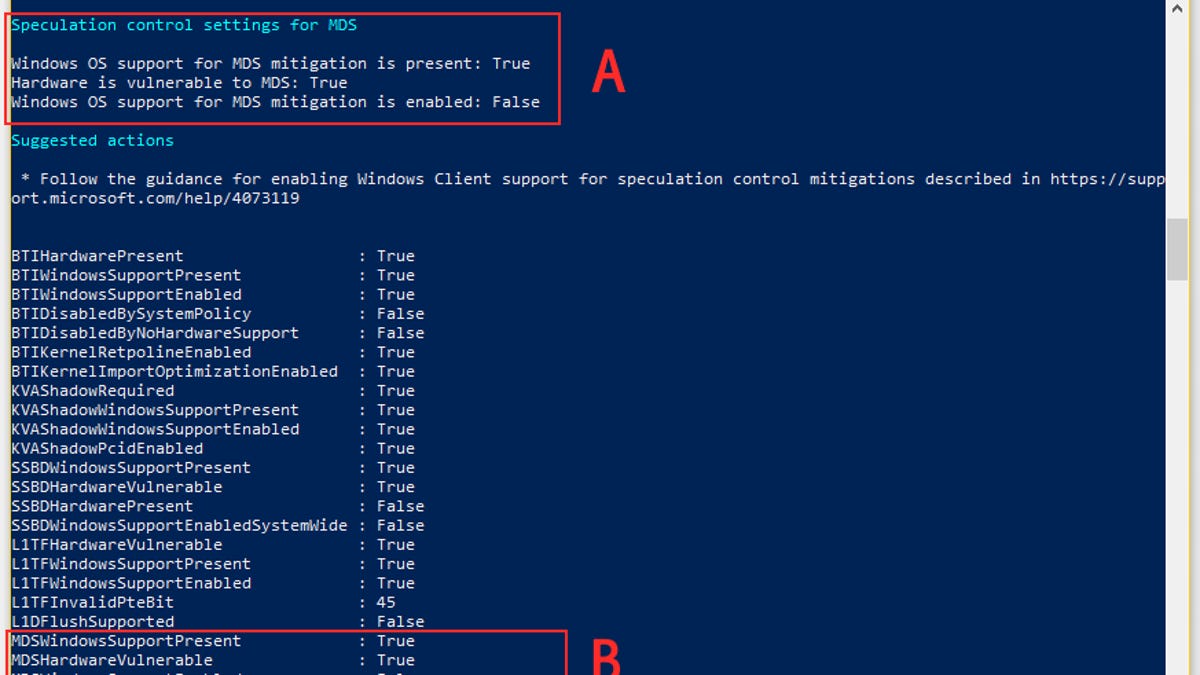
How to test MDS (Zombieload) patch status on Windows systems
PowerShell script tells you if your Windows OS is safe from MDS attacks.
 www.zdnet.com
www.zdnet.com
Yet another serious flaw in Intel chips, and the patches will again have a negative impact on performance, currently estimated around 3% for normal windows users, up to 9% for datacenters and virtualised instances.
In itself, it doesn't seem that bad, but factor in Spectre and Meltdown patches, and we're looking at performance loss over 20%.
This is totally unacceptable.
I won't be buying Intel again until they address these flaws at the hardware level. Remember, even 9th Gen still doesn't patch the Spectre/Meltdown vulnerabilities, they've not done any redesign to mitigate those flaws.
Totally unacceptable imho.
Last edited:


